Unfortunately, many organisations don't have adequate cybersecurity policies or protection measures in place to prevent their operations being compromised by threat actors.
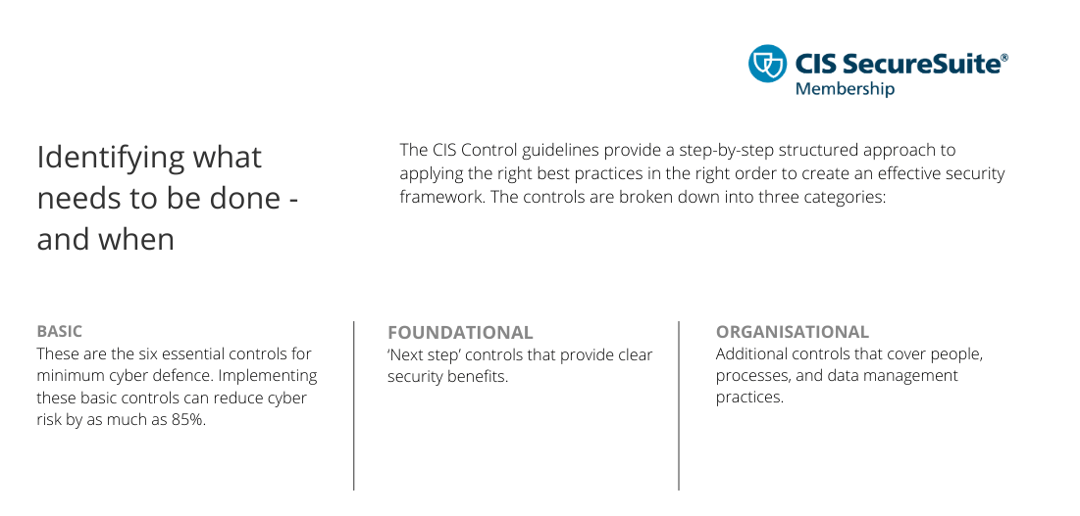
The CIS Controls framework provides a prioritised set of actions that collectively form a defence-in-depth set of practices designed to mitigate the most common attacks against systems and networks.
Going way beyond the much more basic Cyber Essentials recommendations, it provides an ideal foundation for navigating the evolving complexity of the technology ecosystems today’s law firms depend upon.
As an authorised CIS partner, Stridon can help organisations assess and improve their current security state. Delivering a deep understanding of what is critical to the business, data, systems, networks, and infrastructures – and the steps you need to take to protect your IT assets and personnel.
It’s a holistic approach that encompasses every aspect of how you operate. Because cybersecurity has become part of doing business today, it evaluates people, technology and which available safeguards are most appropriate for your environment.
Working through the CIS framework will help:
Understand your risk – undertaking an operational risk assessment, we’ll evaluate your current cyber defence maturity and your IT infrastructure and operations to identify where the vulnerabilities lie.
Identify which defensive steps provide the greatest value – prioritising which controls will provide the greatest risk reduction, so you can build an effective and practical defence.
Understand which controls can be best used to solve which problems – whether that’s detecting indicators of compromise, preventing additional attacks, or planning and executing system backup, incident response and data protection and recovery.
Define and implement a security awareness and training programme – because cybersecurity is a team sport, we’ll help you identify the specific knowledge, skills, and abilities that everyone in the organisation will need. That includes executing a plan to assess and remediate through policy, planning and awareness training.
Prepare a future roadmap – as your infosec requirements evolve, you’ll need to be able to ensure that every aspect of how you operate is covered and that every part of the organisation is protected. Whether that’s ensuring a secure configuration for all endpoints and assets or defining a password policy that’s in line with NCSC guidance. With dependencies expanding, users becoming more mobile, and an extraordinary array of security tools to choose from, we’ll help you.
Combining the Right Tools
When it comes to analysing and improving your data security, we’ll also combine a selection of solutions from leading vendors to ensure that every aspect of your operations is protected, and your top security priorities are addressed.
We don’t believe in a ‘one size fits all’ approach. Every organisation we work with must balance resource constraints with enabling risk mitigation that’s tailored to their unique activities and infrastructure environment. So, it’s vital to deploy the right combination of solutions that will both address organisation risk, and ensure compliance with regulatory responsibilities,
Deploying the right combination of solutions that’s appropriate for the operational model and maintains the confidentiality and integrity of sensitive data is just the start. Everything we select must integrate seamlessly with any existing security measures and deliver a reliable and scalable cyber defence systems that can be evolved in line with changing needs.
Next Steps
We'd be happy to listen to your requirements or challenges, and discuss how we are using this framework with other organisations. Get in touch by calling 020 3006 2140 or email
Related Content:
Countering the Risks of Cybercrime - Why 'defence-in-depth' is the key to securing law firm data